
Let’s say that you’re a miner, and you just found a block.
You want to give yourself an advantage over the rest of the network, so instead of publishing the block through the network and receiving the block reward, you keep your block a secret.
Since you haven’t released your block, you’re effectively the only person working on the most recent block, and you effectively have 100% of the hashpower on your hidden chain.
Nobody else on the network can even attempt to solve the hash puzzle.
This is called selfish mining, or block withholding.
Note that Block withholding is sometimes also used in the context of mining pools, where you submit shares but withhold blocks.
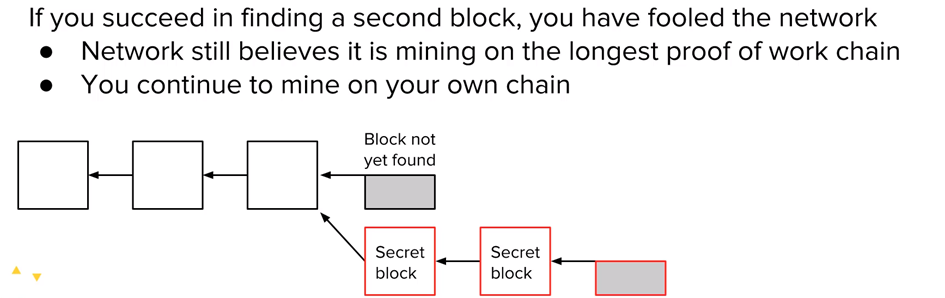
If you find two blocks on your secret chain before the network finds the next one, you suddenly have the longest chain.
The network believes it’s mining on the longest chain, but little does it know that you actually have the longest chain.
You essentially fooled the network.
You’ve guaranteed yourself at least two block rewards because you can just continue to mine on your own chain, assuming that you always stay ahead of the honest network’s chain.
The moment the honest network is about to catch up to you, you can just publish your hidden chain, and then suddenly the honest chain is invalidated, since your chain is the longest, and as we already know, honest nodes in the network will always choose the longest chain.
So, you can continue mining this way and continue cheating the system until the honest network catches up to you.
You’ve guaranteed yourself more block reward than the honest network, and most importantly, you deny the honest network the chance to do any meaningful work because you have your own secret chain, and you can immediately invalidate the honest chain as soon as you publish your secret chain.

So assuming you’re two blocks ahead of the honest network, if the honest network then finds a block, you broadcast your two secret blocks to claim your two block rewards and to keep the honest network from catching up.
This makes the honest network’s block invalid, since the honest chain is now the shorter one.
Because the honest network was mining on chain that was then invalidated, you effectively got time to mine by yourself, for free.
Since you had no competition, you had a higher proportion of the effective hashrate, and therefore, a higher expected return.
The key thing to note here is that you assume that you as a malicious miner can find two blocks faster than the rest of the network can find one block.
If you can’t, then your computation is the one that goes to waste.

What if the network finds a block before you find a second one? Then it becomes a race to propagate the new blocks.
As it turns out, if you have the capability of telling 50% of the network about your block before the other party, as well as greater than 25% of the hashpower, then a malicious strategy is more profitable.
If you have greater than 33% of the hashpower, you can lose the propagation race every time and the malicious strategy will still be more profitable! The math behind these results is omitted here due to complexity, but you’re more than encouraged to look into it!

